Attack Simulation Controls
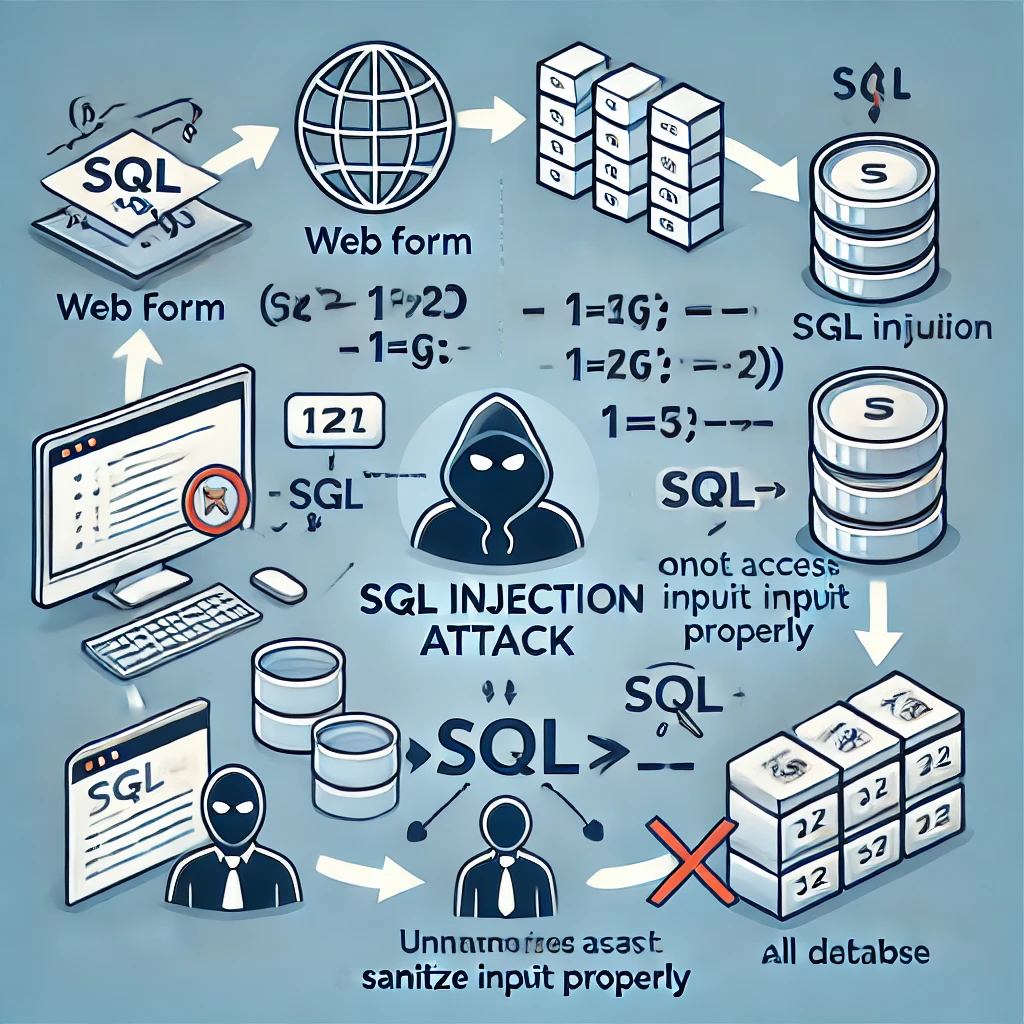
SQL Injection
SQL Injection attacks target vulnerabilities in an application’s database layer by injecting malicious SQL code. It allows attackers to access, modify, or delete data from a database.
Example:
An attacker might input ' OR 1=1; -- into a login form, which could bypass authentication by tricking the SQL query into returning all rows.
How it Works:
Prevention Techniques:
- Use Prepared Statements with Parameterized Queries
- Employ Proper Input Validation
- Use Web Application Firewalls (WAF)
- Least Privilege Database Access
Potential Impacts:
SQL Injection attacks can lead to data breaches, loss of sensitive user information, unauthorized access to systems, and significant financial and reputational damage.
Test Your Knowledge
What is one of the most effective methods to prevent SQL Injection?
- Disabling SQL queries
- Using Parameterized Queries
Malware Attack
Malware attacks involve malicious software that infiltrates, damages, or disables computers, servers, and networks.
Types of Malware:
- Viruses
- Worms
- Trojans
- Ransomware
- Spyware
- Adware
How Malware Works:
Malware can be spread via infected emails, malicious websites, or vulnerabilities in software. Once executed, it may steal data, cause damage, or grant unauthorized access to hackers.

Prevention Techniques:
- Install Antivirus Software
- Keep Systems and Software Updated
- Avoid Clicking on Suspicious Links
- Use a Secure Firewall
Potential Impacts:
Malware can cause data breaches, loss of sensitive information, financial loss, and disruption of services.
Test Your Knowledge
What is one of the most effective methods to protect against malware attacks?
- Ignoring suspicious emails
- Installing antivirus software
Brute Force Attack
Brute Force attacks involve repeatedly trying different combinations of usernames and passwords to gain unauthorized access to a system.
Example:
Attackers automate tools to try millions of password combinations until they successfully guess the correct one.

Prevention Techniques:
- Use Strong Passwords
- Enable Account Lockout After Multiple Failed Attempts
- Implement Multi-Factor Authentication (MFA)
- Monitor Login Attempts for Unusual Activity
Potential Impacts:
Brute Force attacks can lead to unauthorized access to systems, data theft, or account compromise.
Test Your Knowledge
What is one of the most effective methods to protect against Brute Force attacks?
- Using a weak password
- Enabling Multi-Factor Authentication (MFA)
DoS Attack
A Denial of Service (DoS) attack aims to make a system or service unavailable by overwhelming it with traffic, leading to slowdowns or crashes.
How It Works:
Attackers flood a network or service with traffic, consuming all available resources, and leaving it unable to respond to legitimate requests.

Prevention Techniques:
- Use Load Balancers and Firewalls
- Implement Traffic Monitoring and Rate Limiting
- Deploy Anti-DDoS Services
Potential Impacts:
DoS attacks can cause significant service disruptions, loss of revenue, and customer dissatisfaction.
Test Your Knowledge
What is a key method to prevent a DoS attack?
- Ignoring traffic spikes
- Using Load Balancers and Firewalls
DDoS Attack
A Distributed Denial of Service (DDoS) attack is similar to a DoS attack, but it uses multiple systems to flood the target with traffic from many sources, making it harder to block.
How It Works:
Attackers use a network of infected devices (botnets) to send massive amounts of traffic to overwhelm the target's servers.

Prevention Techniques:
- Deploy Anti-DDoS Services
- Use IP Whitelisting
- Monitor and Mitigate Traffic in Real-Time
Potential Impacts:
DDoS attacks can take down websites and online services, resulting in service outages, reputational damage, and financial loss.
Test Your Knowledge
How can you mitigate a DDoS attack?
- Ignore it
- Use Anti-DDoS Services
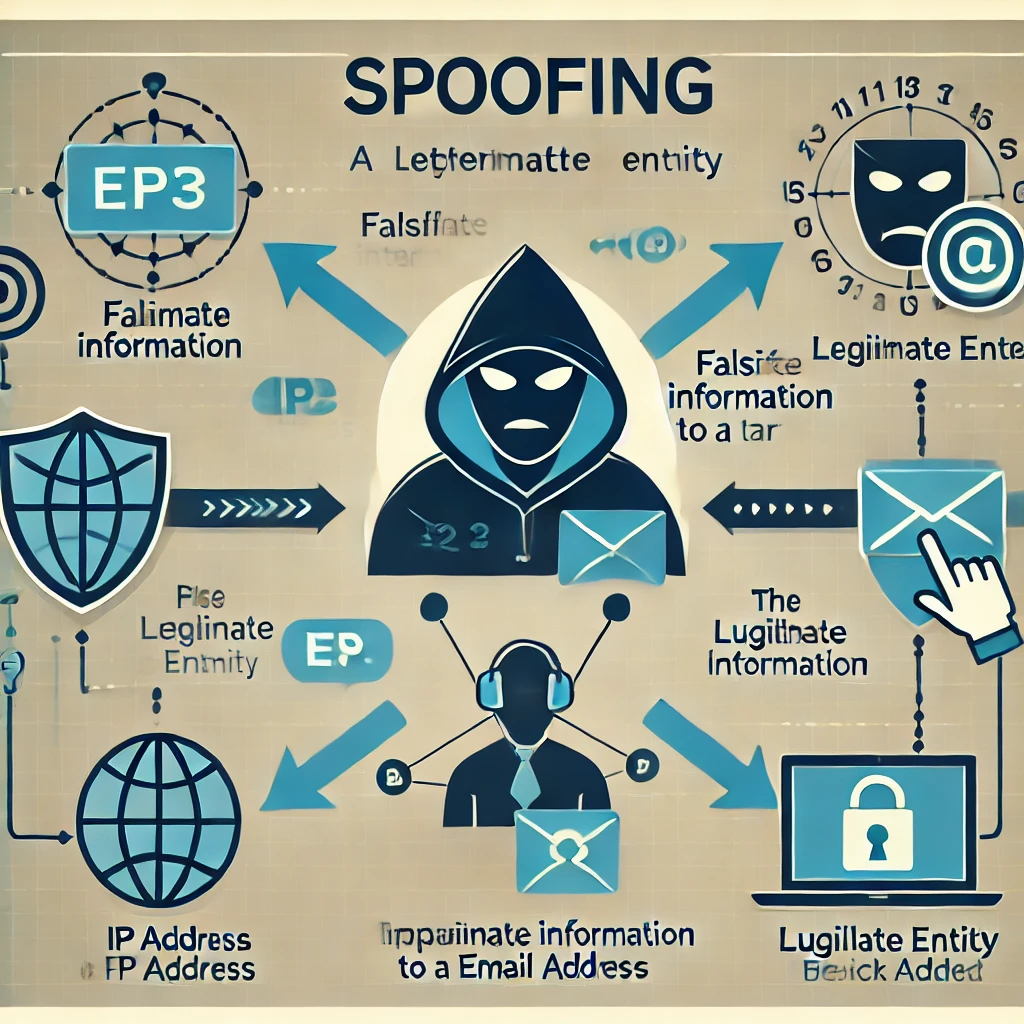
Spoofing Attack
Spoofing attacks involve pretending to be another entity, such as by falsifying IP addresses or emails, to deceive the target and gain unauthorized access or information.
Prevention Techniques:
- Implement Email Authentication Mechanisms (SPF, DKIM)
- Verify IP Addresses with Firewalls
- Use Anti-Spoofing Software
Potential Impacts:
Spoofing attacks can lead to phishing scams, data theft, and impersonation of trusted entities.
Test Your Knowledge
How can you protect against email spoofing?
- By ignoring suspicious emails
- Using Email Authentication Mechanisms
XSS Attack
Cross-Site Scripting (XSS) attacks inject malicious scripts into trusted websites, which then run on the victim's browser to steal data or manipulate content.

Prevention Techniques:
- Sanitize User Input
- Use Content Security Policy (CSP)
- Validate Output to Ensure It Cannot Contain Harmful Scripts
Potential Impacts:
XSS attacks can steal sensitive data, take over user sessions, or manipulate website content.
Test Your Knowledge
How do you prevent Cross-Site Scripting (XSS) attacks?
- Ignoring input validation
- Sanitizing User Input
API Attack
API attacks target vulnerabilities in application programming interfaces (APIs), allowing attackers to exploit API flaws to gain unauthorized access or disrupt services.
Example:
An attacker may exploit a poorly secured API endpoint to extract sensitive data, bypass authentication, or overload the API with requests.
How It Works:
APIs serve as intermediaries between different software applications. Attackers can exploit unsecured API endpoints, often using automated tools, to manipulate the functionality, access data, or disrupt services.

Prevention Techniques:
- Use API Gateways and Authentication
- Validate Input and Output Data
- Implement Rate Limiting to Prevent Overuse
- Encrypt Data in Transit
Potential Impacts:
API attacks can lead to unauthorized data access, loss of sensitive information, and disruption of services.
Test Your Knowledge
What is one of the most effective methods to protect APIs from attacks?
- Not using an API
- Using API Gateways and Authentication